
The Secret to Creating High-Quality Custom Apps
January 14, 2022
The Ultimate Guide to Performing Cloud Audits
January 14, 2022
The Ultimate Guide to hiring the best Cyber Security and Compliance engineers

With so many hacking incidents and other security breaches making it to the headlines, cyber security is at the top of the mind of every senior executive out there. However, the fact is that most organizations are woefully understaffed when it comes to their compliance program. Cyber security is a specialization very few businesses have the budget to hire specialists for, but it is essential to your company’s future to get these right. Read on to learn more about how you can protect your organization.
Cyber Security and Compliance: Overview

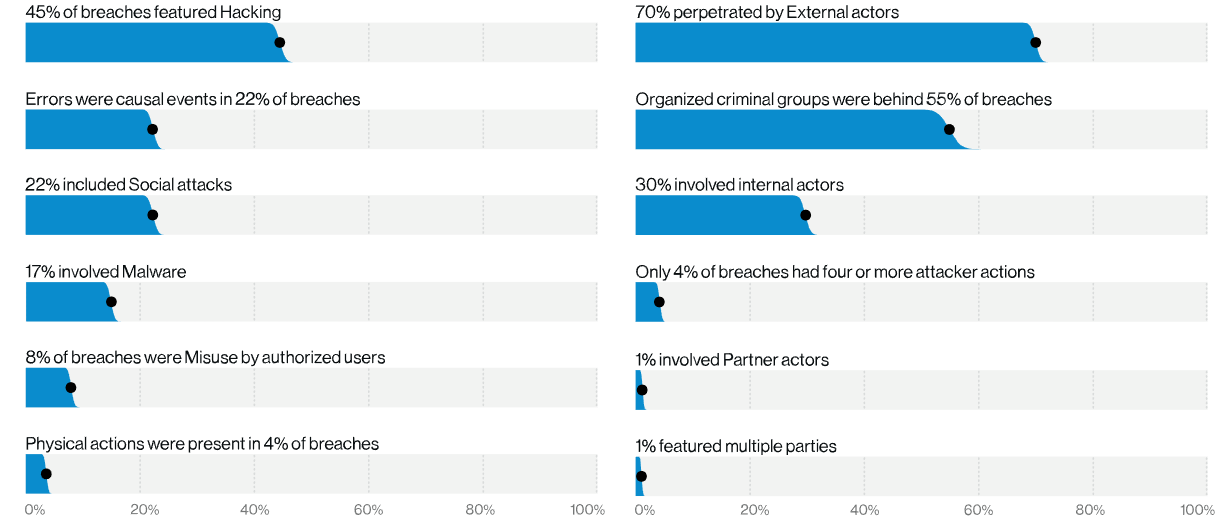
Cybersecurity is the practice of protecting systems, networks, and programs from digital and physical exploitation. Cyber attacks are typically aimed at gaining access to sensitive data or merely disrupting routine business operations for extortion. There are broadly four types of Cybersecurity threats:
- Phishing: Phishing refers to an attack where the attacker masquerades as a trusted entity, tricks someone into clicking on a link that directs them to a website that might seem legitimate at first glance, and hopes to steal login credentials and payment information of the user.
- Ransomware: Ransomware is malicious software used to prevent an organization from accessing critical data unless a ransom is paid.
- Malware: Malware is a type of software designed to either cripple a system/network or gain unauthorized access to it.
- Social Engineering: Social engineering refers to a set of techniques used by an attacker to trick you into revealing sensitive information or, at times, impersonating you to gain access to critical data.
Cybersecurity compliance refers to meeting standards set by a regulatory agency, law, or industry to shelter sensitive data from attackers. The sensitive data in question can be anything ranging from personally identifiable information(PII) such as first and last name, home address, social security number(SSN) to protected health information(PHI) like medical history or prescription records to even financial information such as credit card/ debit card numbers, credit history, and ratings. Compliance requirements depend a lot on the industry your organization is working in. For instance, a company operating in the Pharma industry must meet the criteria set by the FDA. Compliance requirements often overlap as well. If the particular pharma company in question accepts payments through a Point-of-service(POS) device, it must also meet the Payment card industry data security standard(PCI DSS) requirements. Compliance requirements can be region-specific, like the GDPR in the EU or PIPL in China.
How does it affect your organization?
Cybersecurity is something that can either make or break your organization. The impacts of a cyberattack can be catastrophic even. It can lead to substantial economic and goodwill losses and not to mention the potential legal implications. An attack on your network leaves you vulnerable since the attacker can access corporate, financial, and other sensitive information that you don’t want out in public. The colonial fuel hack exhibited how hacks that can cost companies millions of dollars can be prevented by investing in Cybersecurity training.
The value gained by investing in providing basic Cybersecurity training to all employees far outweighs the cost. Establishing some basic Cybersecurity principles for your organization, such as a network/internet/email use policy, can also prove beneficial. Maintaining logs of remote access requests and managing internal data well can prove to be a deciding factor in how quickly you can detect a data breach.
Understanding the compliance requirements for a data privacy

Data privacy compliance refers to regulations a business must abide by to protect the sensitive data it possesses. These regulations can be in the form of industry standard or federal or state laws or even in the form of global regulations such as the GDPR.
At this point, there is no single principal data protection legislation in the US. However, there are hundreds of laws enacted on both the state and federal levels. However, the Federal Trade Commission Act empowers the U.S FTC to pursue action against unfair or deceptive practices. And the FTC has made it clear with the action against big tech that they have every intention of protecting data privacy rights.
Getting the Job: Why Hire a Cyber Security and Compliance Engineer?
Mammoth companies like Microsoft, MGM resorts, Magellan Health and Twitch have been affected by Cyber Attacks over the past year. Cyber security engineers are responsible for the security measures undertaken by your organization to prevent attacks to protect your core business. Even though Cybersecurity is a shared responsibility across the organization, it is important to have someone to lead the effort. Cybersecurity engineers perform penetration tests on your network to test and fix any vulnerabilities that might arise. They can prove to be incredibly valuable when trying to make sense of a security breach. Here are some specialist areas in Cybersecurity talent:
- Penetration Testing
- Security Analysis
- Incident Response
What to Look for in a Cyber Security Engineer
Talented Cyber Security engineers come by really hard, and it is imperative to know what you’re looking for when you’re trying to hire one. The top skills required for a Cyber Security professional are:
- Technical Aptitude
- Security incident Handling
- Audit and Compliance
- Firewall/IDP/IDS skills
- Digital forensics
- Access Management
- Penetration Testing
- Risk Assessment
How Atidan Technologies can help you hire the best Cybersecurity and Compliance engineers for your business

Atidan has access to the largest talent pool in the world with a proven track record of customer satisfaction. Atidan provides result-oriented staffing services so that you can focus on your running business. We have highly experienced recruiters with a strong technical background across North America, EU, and APAC time zones. Atidan boasts of high retention rates for all vetted candidates. With over eight years of experience in staffing and global offices in the USA, UK, India, SEA, and success stories across various industries, Atidan can manage all your hiring needs

