
How Cloud Computing is Transforming Data Mining for Business Intelligence
February 15, 2022
How to Implement a Zero Trust Security Strategy in an Enterprise Environment
February 16, 2022
How FinOps Can Help You Beat Out Major Competitors in Cloud Cost Optimization

The primary goal of FinOps is to increase the business value derived from cloud spending by implementing best practices while consolidating finance and IT. Cloud computing provides many opportunities for efficiency, but at the same time it can create organizational-level inefficiencies because of a lack of a clear understanding of cloud usage and spending at the management level. According to the HashiCorp State of Cloud Strategy Survey, as much as 40% of the respondent organizations stated that they categorically overspent when it came to cloud spending. This is a serious cause for concern and calls for the implementation of adequate spending governance so as to thwart overspending but not crush innovation. Here’s everything you need to know about FinOps.
Introduction to FinOps and Cloud Cost Optimization

FinOps is a collection of best practices, organizational processes, and solutions for managing cloud expenditures and bringing financial accountability to cloud spending. It focuses on optimizing cloud spending and making tradeoffs by looking at things from a business standpoint. It lays emphasis upon understanding the cloud usage and cost structures within the organization. It can also involve setting budgets for cloud usage and ensuring that they are enforced properly. It also focuses on promoting accountability when it comes to cloud usage within the organization. FinOps efforts across organizations must abide by the following principles:
- Effective collaboration between teams.
- Driving cloud decisions based on business value.
- Promotion of ownership for cloud usage amongst employees.
- FinOps reports must be prepared timely and be easily accessible.
- Creation of a centralized team that drives FinOps efforts.
- Taking advantage of the variable cost model of the cloud.
The Three Phases of FinOps
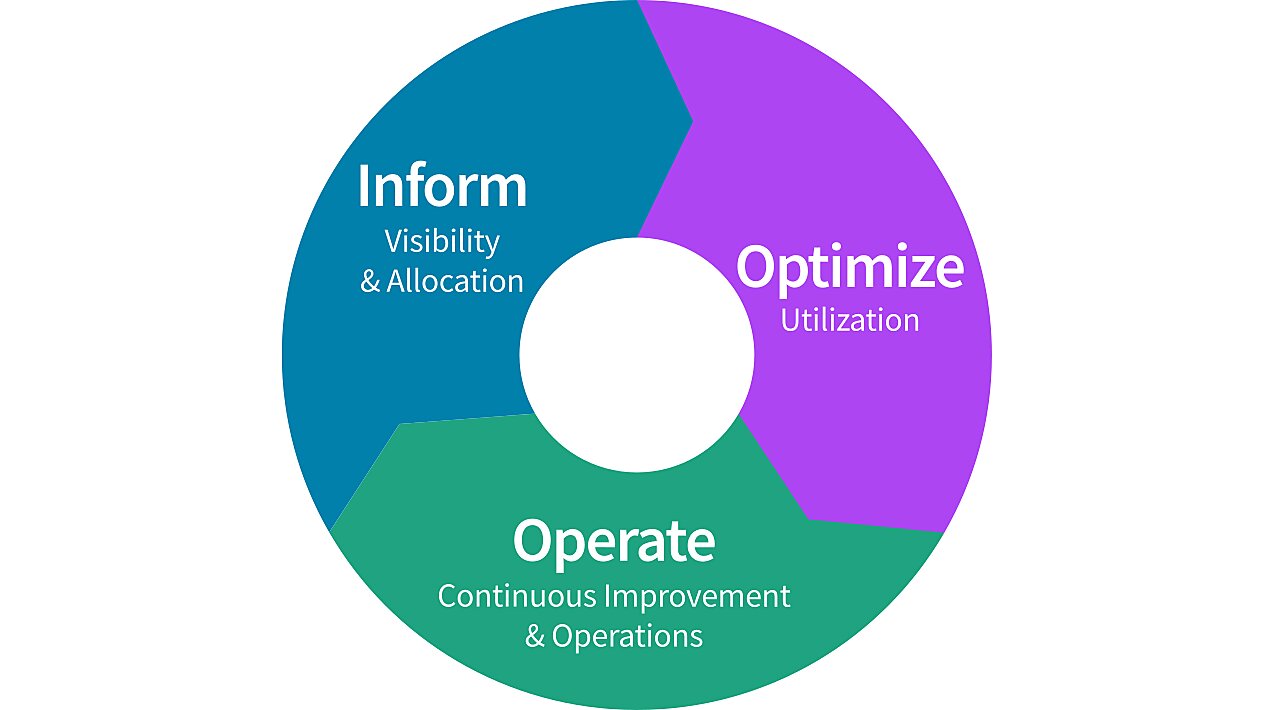
The FinOps journey can be divided into three iterative phases: inform, optimize, and operate. It is important to acknowledge that this is not a chronological representation of the FinOps implementation journey given that these phases are not necessarily operated upon in any specific order or even just once. FinOps is an iterative process and the journey to cost optimization of cloud spending might vary greatly from one organization to another. Each FinOps team will have to revisit and review the three stages to ensure the circumvent overspending. Here’s everything you need to know about the different phases:
- Inform: The first phase in the FinOps journeys lays emphasis upon improving visibility of cloud expenditure. It involves maintaining proper documentation of all cloud usage to avoid an accounting nightmare. Customized pricing and discounts are very common in the cloud computing industry and therefore, it is imperative that teams receive budgeting and allocation guidelines which must then be strictly enforced. Benchmarking tools must be used and KPI(s) must be established to enable accurate benchmarking and promote efficiency.
- Optimize: This is the phase where the existing cloud expenditure is observed carefully and emphasis is laid upon effective planning which reduces the utilization of on-demand resources which can drive up cloud spending. Organizations must create an inventory of all the services being utilized and automating spending cuts to promote judicious use of resources.
- Operate: This phase involves effective tracking of business objectives against the metrics that are being tracked against those objectives. It can help understand whether teams are optimizing for the right metric or not. A channel of communication between the executive management and the IT team is established which is often referred to as the Cloud cost center of excellence.
FinOps: The Challenge

While the cloud can enable innovation and agility, it's all too simple to lose control over costs in the process. Traditional businesses find it harder to get accustomed to the FinOps model given that it can be incredibly hard for the management team to understand the variable cost structures associated with the cloud model. Here are some common problems associated with FinOps implementations:
- Innovation: In the modern world where updates and bug fixes must be shipped as swiftly as possible, there is a lack of acknowledgement amongst development teams for how much it can impact the business financially. Nevertheless, it is important to encourage innovation within the organization to empower employees to create new solutions that could possibly produce a non-linear return on investment for the organization.
- Dynamic nature of cloud pricing: Cloud pricing is dynamic in nature and subject to change according to demand and supply dynamics. It is generally hard to predict the cost structures in advance. What makes matters worse is the lack of visibility which makes implementing chargebacks a great ordeal.
- Inability to adequately quantify wasteful spending: Wasteful spending estimates are well, estimates. It is incredibly hard to accurately determine what spending can be categorized as wasteful spending.
- Lack of effective collaboration: The lack of communication between the management and development teams can be a huge problem when trying to optimize cloud costs. A sudden shift in focus on the business side can have huge implications on the cloud bill.
How Atidan Technologies Can Help In Your FinOps Journey

Atidan specializes in helping your business realize its true potential with the help of the latest technologies to make sure that you come out ahead. With decades of experience and a tremendously powerful platform, our goal is to help you realize the full potential of today's cutting-edge technologies. With a presence in over 14 countries, We have software engineers that can help you maximize your technology investments and bring new efficiencies to your business. Our team of developers, architects, and specialists bring a diverse array of technology frameworks and a rock-solid approach to ensure your application works seamlessly. In addition, Atidan’s expert consultants will work actively with your business process managers, IT staff, and executive leadership to identify your requirements and help you reach your business goals. Managing your cloud resources well and stopping any overspending can be made easy with the help of Atidan.

